Types of Software and Interrupts
Features of System Software
- Set of programs to control and manage the operation of computer hardware.
- Provides a platform on which other software can run.
- Required to allow hardware and software to run without problems
- Provides a human computer interface
- Controls the allocation and usage of hardware resources.
From Text Books
Features of Application Software
- used to perform various applications (apps) on a computer
- Allows a user to perform specific tasks using the computer’s resources
- May be a single program (for example, NotePad) or a suite of programs (for example, Microsoft Office)
- User can execute the software as and when they require.
From Text Books
Examples of Application Software
From Past Papers
Word Processor:
Word processing software is used to manipulate a text document, such as an essay or a report
Spreadsheets:
Spreadsheet software is used to organize and manipulate numerical data (in the form of integer, real, date, etc). Numbers are organised on a grid of lettered columns and numbered rows.
Database:
Database software is used to organise, manipulate and analyse data. Tables consist of rows and columns. Each row is called a ‘record’ and each column is called a ‘field.
Photo Editing Software:
Photo editing software allows a user to manipulate digital photographs stored on a computer; for example, change brightness, change contrast, alter colour saturation or remove “red eye”
Control And Measuring Software:
Control and measuring software is designed to allow a computer or microprocessor to interface with sensors.
Video Editing Software:
Video editing software is the ability to manipulate videos to produce a new video. It enables the addition of titles, colour correction and altering/adding sound to the original video
Examples of System Software
From Past Papers
Compilers:
A compiler is a computer program that translates a program written in a high-level language (HLL) into machine code (code which is understood by the computer)
Linkers:
A linker (or link editor) is a computer program that takes one or more object file produced by a compiler and combines them into a single program.
Device Drivers:
A device driver is the name given to software that enables one or more hardware devices to communicate with the computer’s operating system.
Operating System:
The operating system (OS) is essentially software running in the background of a computer system. It manages many of the basic functions.
Utilities:
Utility programs are software that are designed to carry out specific tasks on a computer.
- anti-virus (virus checkers)
- anti-spyware
- back-up of files
- disk repair and analysis
- file management and compression
- security
- screensavers
- disk defragmenter/ defragmentation software.
Antivirus Software
- Antivirus checks software or files before they are run or loaded on a computer.
- Antivirus software compares a possible virus against a database of known viruses.
- They carry out heuristic checking – this is the checking of software for types of behaviour that could indicate a possible virus; this is useful if software is infected by a virus not yet on the database.
- Any possible files or programs which are infected are put into quarantine this allows the virus to be automatically deleted, or user to make the decision about deletion. (Sometimes a file which doesn’t contain a virus can be flagged as one. This is called false positive)
- Anti-virus software needs to be kept up to date since new viruses are constantly being discovered.
- Full system checks need to be carried out once a week, for example, since some viruses lie dormant and would only be picked up by this full system scan.
From Text Books
Defragmentation software
As a HDD becomes full, blocks used for files will become scattered all over the disk surface. The HDD read-write head will now require several movements just to find and retrieve the data making up the required file. A disk defragmenter will rearrange the blocks of data to store files in contiguous sectors wherever possible. This allows for much faster data access and retrieval since the HDD will now require fewer read-write head movements.

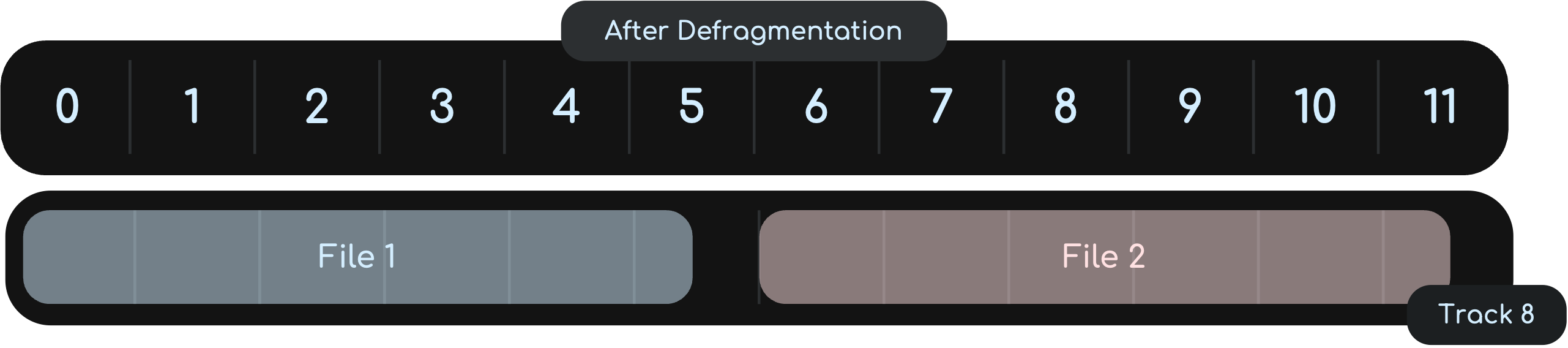
From Text Books
Back-up Software
A back-up Utility allows you to set a schedule for backing up files and only carry out a back-up procedure if there have been any changes made to a file. 3 Back-ups should be made for total security.
- The current (working) version stored on the internal HDD or SSD
- A locally backed up copy of the file (stored on a portable SSD)
- A remote back-up version stored well away from the computer (for example, using cloud storage).
A locally backed up copy could be used when internet is not available. A remote back-up of a file is useful when a computer stops working (hardware or software fault)
From Text Books
Security software
Security software is a utility that:
- Manages access control and user accounts (using user IDs and passwords)
- Links into other utility software, such as virus checkers and spyware checkers
- Protects network interfaces (for example, through the use of firewalls)
- Uses encryption and decryption to ensure any intercepted data is meaningless without a decryption key
- Oversees the updating of software (does the update request come from a legitimate source, for example).
From Text Books
Screen-saver Software
Screensavers are used as part of the computer’s security system. If a computer is unused for five minutes, for example, and hasn’t been logged out, this will trigger the screensaver to be loaded. The computer user will then be automatically logged out and a screensaver will indicate that the computer is now locked.
Screensavers are also used to activate useful background tasks, here are examples:
- Virus scans
- Distributed computing applications – these allow apps to use the computer’s resources only when it is idle.
From Text Books
Device Driver software
Device drivers are software that communicate with the operating system and translate data into a format understood by a hardware peripheral device. As soon as a device is plugged into a USB port, the operating system looks for the appropriate device driver. All USB device drivers contain a collection of information about devices called descriptors; this allows the USB bus to ask a newly connected device what it is. Descriptors include vendor id (VID), product id (PID) and unique serial numbers.
From Text Books
Operating System
Functions of Operating System
- Human computer interface (HCI)
- Multitasking
- Platform for running of application software.
- Management of user accounts
- Managing files
- Hardware peripheral management (including drivers)
- Memory management
- Interrupt handling routines
- Security (manages log on, passwords)
From Text Books
Human Computer Interface (HCI)
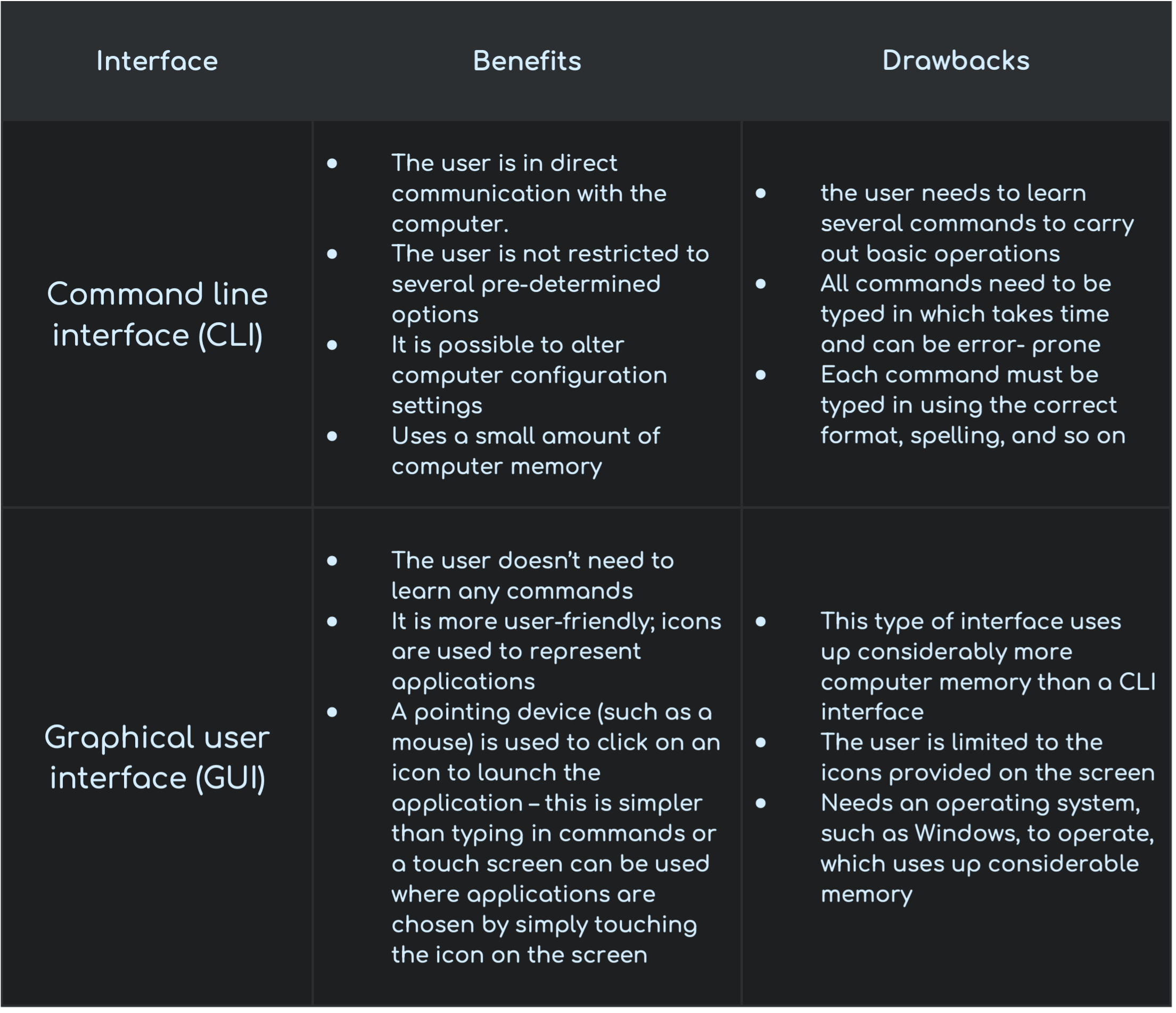
The human computer interface (HCI) is in the form of a Command Line Interface (CLI) or a Graphical User Interface (GUI).
A CLI requires a user to type in instructions to choose options from menus, open software, etc. There are several commands that need to be typed in, for example, to save or load a file. The user must learn several commands just to carry out basic operations.
A GUI allows the user to interact with a computer using pictures or symbols (icons) rather than having to type in a number of commands.
From Text Books
Human Computer Interface (HCI)
CLI: a programmer, analyst or technician; someone who needs to have a direct communication with a computer to develop new software, locate errors and remove them, initiate memory dumps (contents of the computer memory at some moment in time), and so on
GUI: the end-user who doesn’t have or doesn’t need to have any great knowledge of how the computer works; a person who uses the computer to run software or play games or stores/manipulates photographs, for example.
From Text Books
Security Management
- Human computer interface (HCI)
- Multitasking
- Platform for running of application software.
- Management of user accounts
- Managing files
- Hardware peripheral management (including drivers)
- Memory management
- Interrupt handling routines
- Security (manages log on, passwords)
From Text Books
Hardware Peripheral Management
- Communicates with all input and output devices using device drivers.
- Uses a device driver to take data from a file (defined by the operating system) and translates it into a format that the input/output device can understand.
- Ensures each hardware resource has a priority so that they can be used and released as required.
- Manages input/output devices by controlling queues and buffers; consider the role of the printer management when printing out a document:
- First of all, the printer driver is located and loaded into memory
- then the data is sent to a printer buffer ready for printing
- If the printer is busy (or the printing job has a low priority) then the data is sent to a printer queue before it can be sent to the printer buffer – it will send various control commands to the printer throughout the printing process.
- It receives and handles error messages and interrupts from the printer.
From Text Books
File Management
The main tasks of file management include:
- File naming conventions which can be used i.e. filename.docx (where the extension can be .bat, .htm, .dbf, .txt, .xls, etc.)
- Performing specific tasks (for example, create, open, close, delete, rename, copy, and move)
- Maintaining the directory structures
- Ensuring access control mechanisms are maintained (for example, access rights to files, password protection, or making files available for editing or locking them)
- Ensuring memory allocation for a file by reading it from the HDD/SSD and loading it into memory
From Text Books
Multitasking
Multitasking allows computers to carry out more than one task (i.e. a process) at a time. Each of the processes will share the hardware resources under the control of the operating system software.
- Resources are allocated to a process for a specific time limit.
- The process can be interrupted while it is running.
- The process is given a priority so it can have resources according to its priority (the risk here is that a low priority process could be starved of resources).
From Text Books
Management of User Accounts
From Past Papers
Computers allow more than one user to log onto the system. It is therefore important that users’ data is stored in separate parts of the memory for security reasons. Each person logging onto the computer will be given a user account protected by a username and password. This allows each user to:
- Customize their screen layout and other settings.
- Use separate folders and files and to manage these themselves.
Running of Applications
From Past Papers
Upon initiating, a computer undergoes a process known as booting (Bootstrap loader), during which a part of the operating system must be transferred to RAM. This operation, is managed by the basic input/output system (BIOS), which oversees the startup of the computer’s motherboard. The BIOS instructs the computer on the location of the storage device housing the operating system, proceeds to load the essential portion of the operating system, and subsequently executes it.
The BIOS is often referred to as firmware. Firmware is defined as a program that provides low level control for devices.
Interrupts
From Past Papers
An interrupt is a signal transmitted from either a device or software to the microprocessor, prompting the microprocessor to temporarily halt its current operations in order to address and respond to the interrupt.
- An input/output process (for example, a disk drive or printer requiring more data)
- A hardware fault (for example, a paper jam in the printer)
- User interaction (for example, the user presses a key (or keys) on a keyboard, such as <CTRL><ALT><BREAK>, which causes the system to be interrupted)
- Software errors that cause a problem
When an interrupt signal is received, the microprocessor pauses its current task to deal with the interrupt. The computer needs to figure out what type of interrupt it is and how important it is.
Interrupts help computers do many things at once or have multiple windows open. For example, you can download a file while listening to music, and interrupts make it seem like both things are happening at the same time. In reality, data moves quickly in and out of memory, This is possible due to a temporary storage area called a buffer.
Programming language, translators and (IDEs)
Difference Between High and Low Level Languages
From Text Books

Advantages of Assembly languages
- To make use of special hardware
- To make use of special machine-dependent instructions
- To write code that doesn’t take up much space in primary memory
- To write code that performs a task very quickly
From Text Books
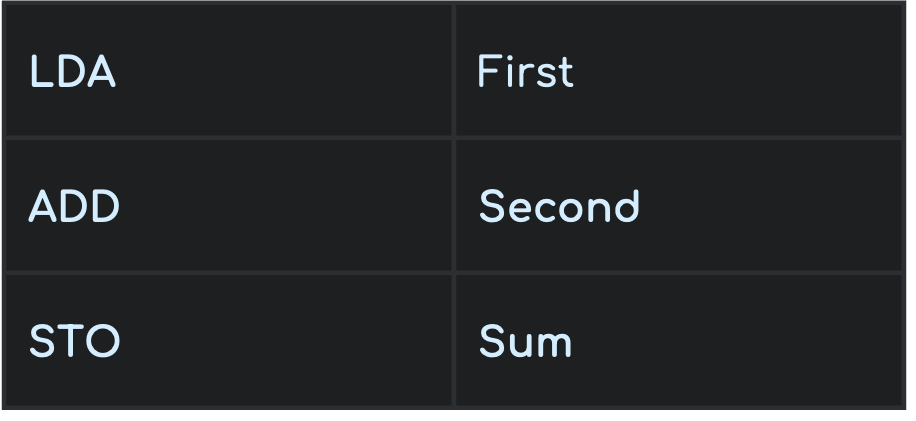
Compilers
A compiler is a software that converts a full program written in a high-level language into machine code in a single operation. After compilation, this machine code can be reused for the same task multiple times without needing re-compilation. If errors are found, an error report is generated instead of a compiled program.
From Text Books
Interpreters
An interpreter is a computer program that reads a statement from a high-level language program, translates it, executes the specified action, and repeats this process for each subsequent statement. If there is an error in a statement, the execution stops, and an error message is displayed. Unlike a compiler, a program requires interpretation each time it is run.
From Text Books
Assemblers
An assembler is a computer program that converts a program written in assembly language into machine code, allowing direct use by a computer. Once a program is assembled, the resulting machine code can be repeatedly used to execute the same task without requiring re-assembly.
From Text Books
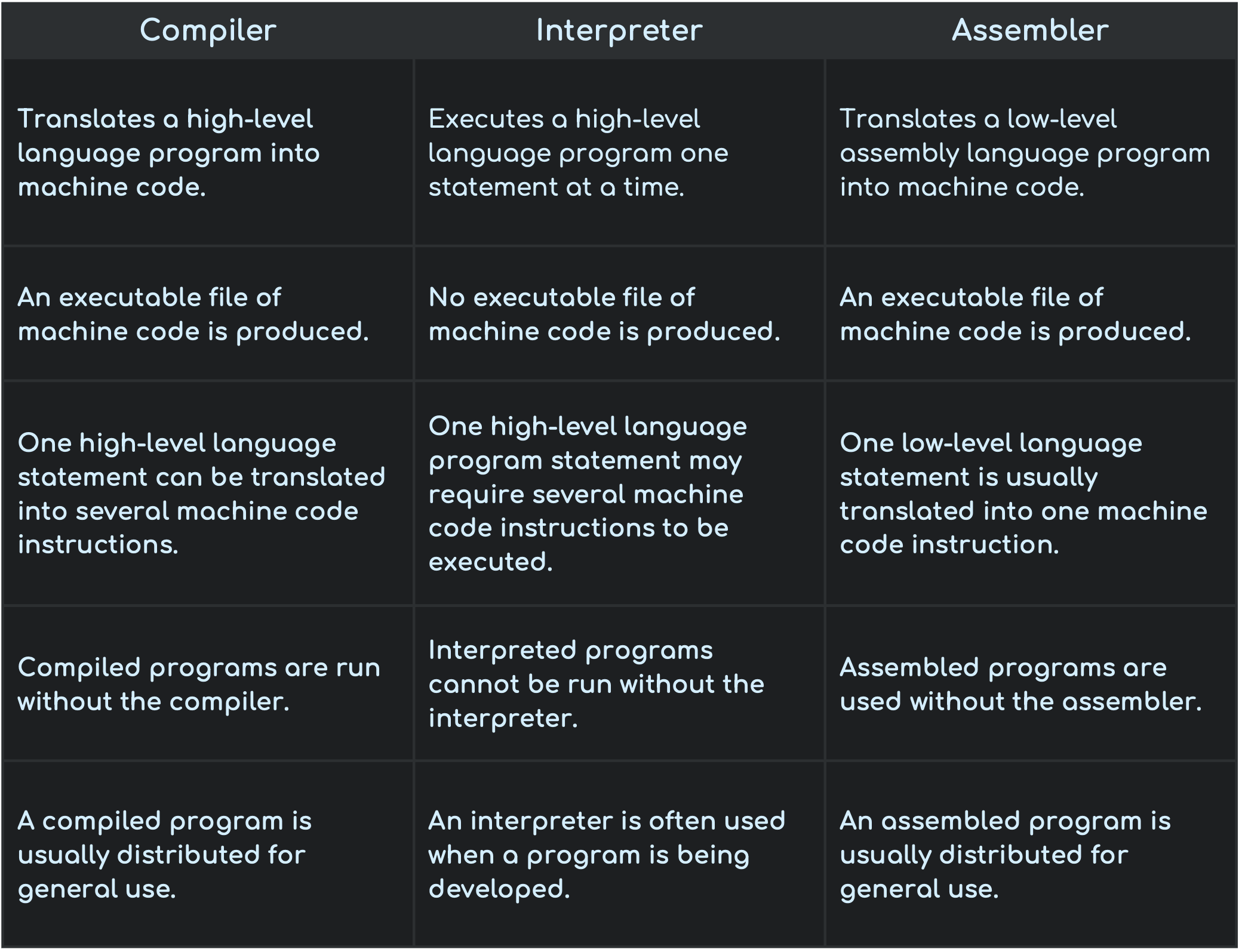
Comparision between Compilers, Interpreters and Assemblers
From Text Books
Features of an Integrated Development Environment
- Code editors
- A translator
- A runtime environment with a debugger
- Error diagnostics
- Auto-completion
- Auto-correction
- An auto-documenter
- Pretty printing.
From Text Books
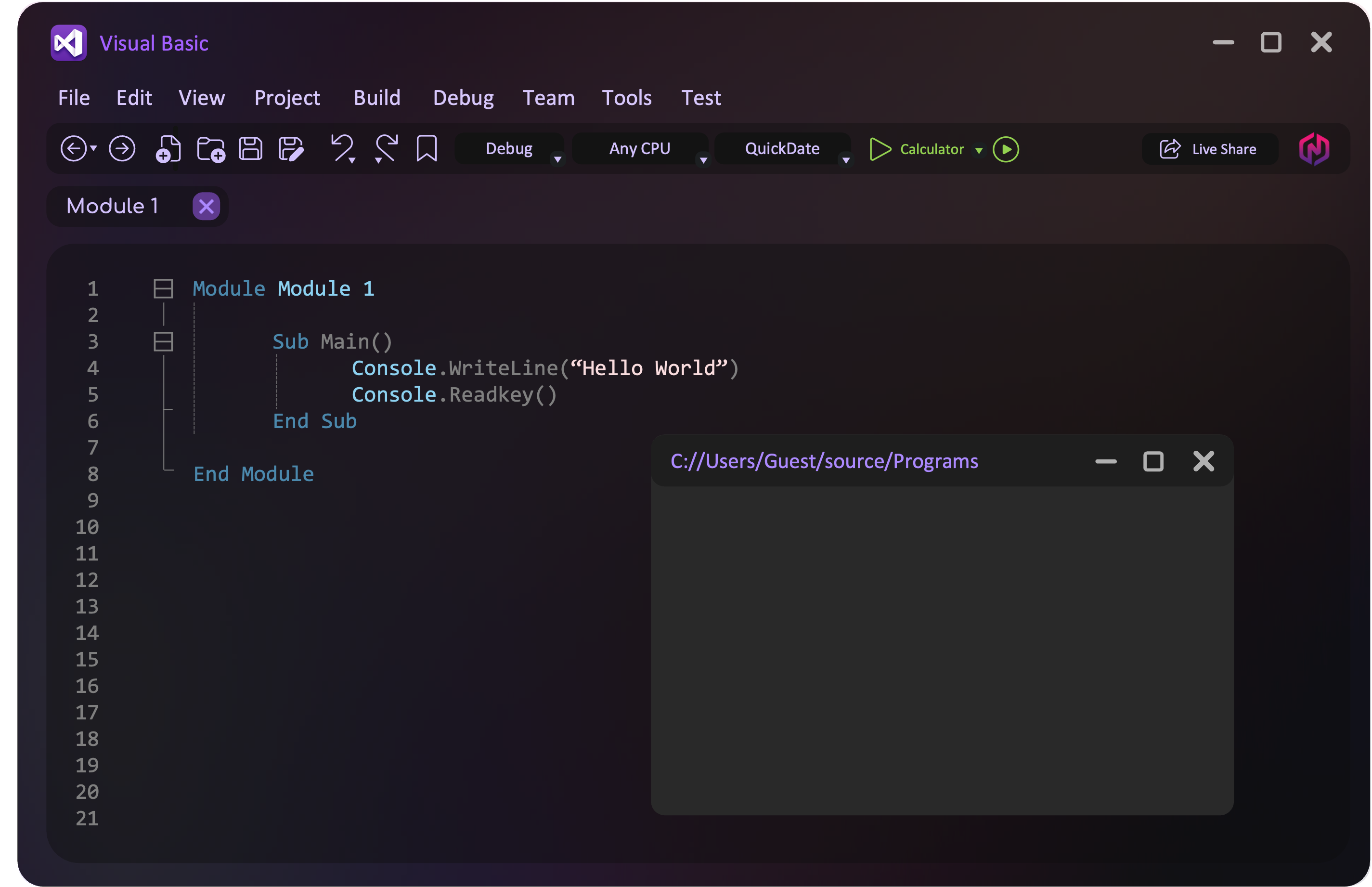
Code Editor
A code editor lets you write and edit a program without having to switch to another text editor. This speeds up the process because you can make changes directly within the same software.
From Text Books
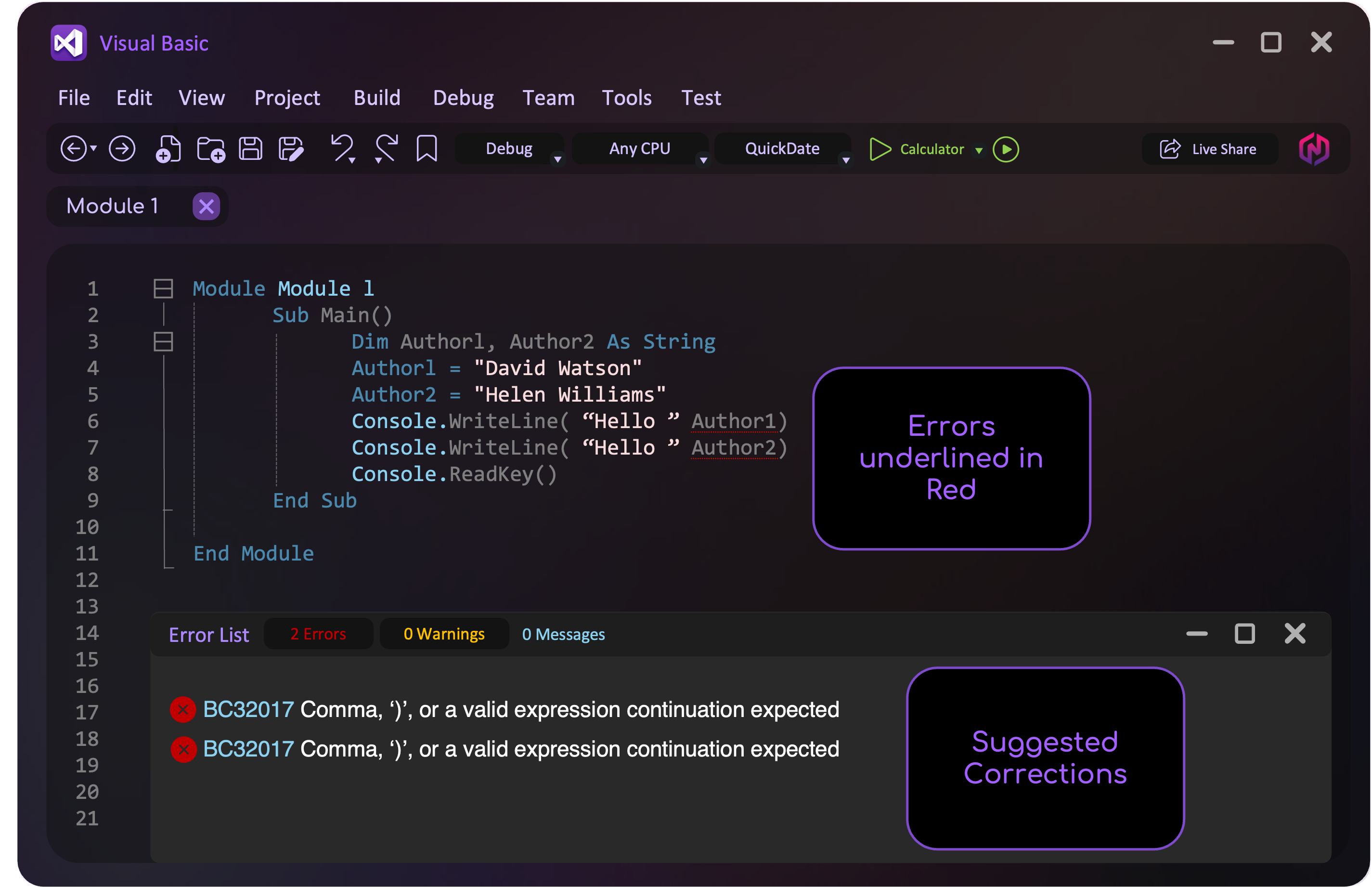
Error Diagnostics and auto-correction
Dynamic error checking catches possible mistakes as you type the program code. It notifies you right away and suggests a correction. This helps find and fix errors while you’re still working on the program, before running it.
From Text Books
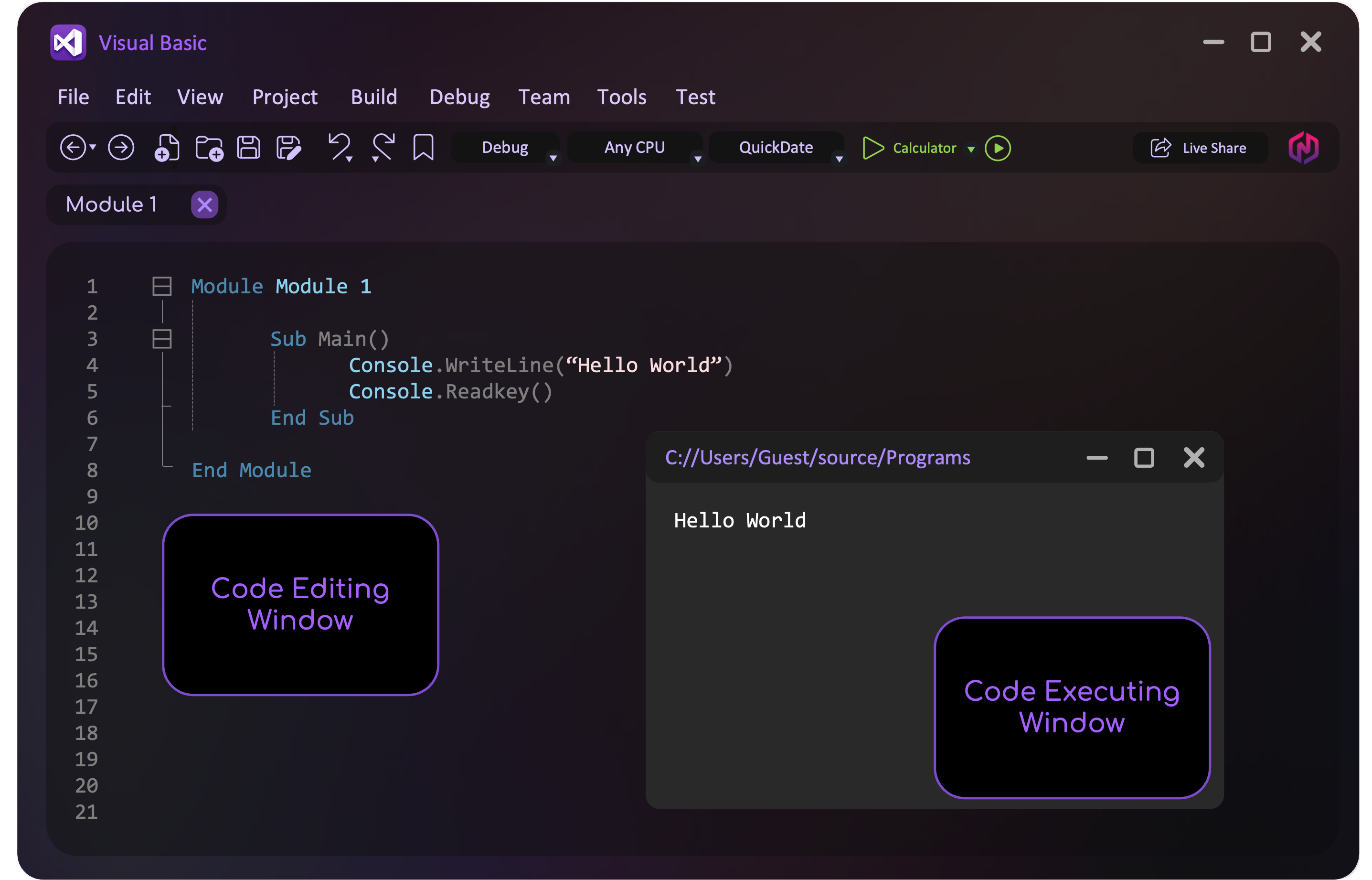
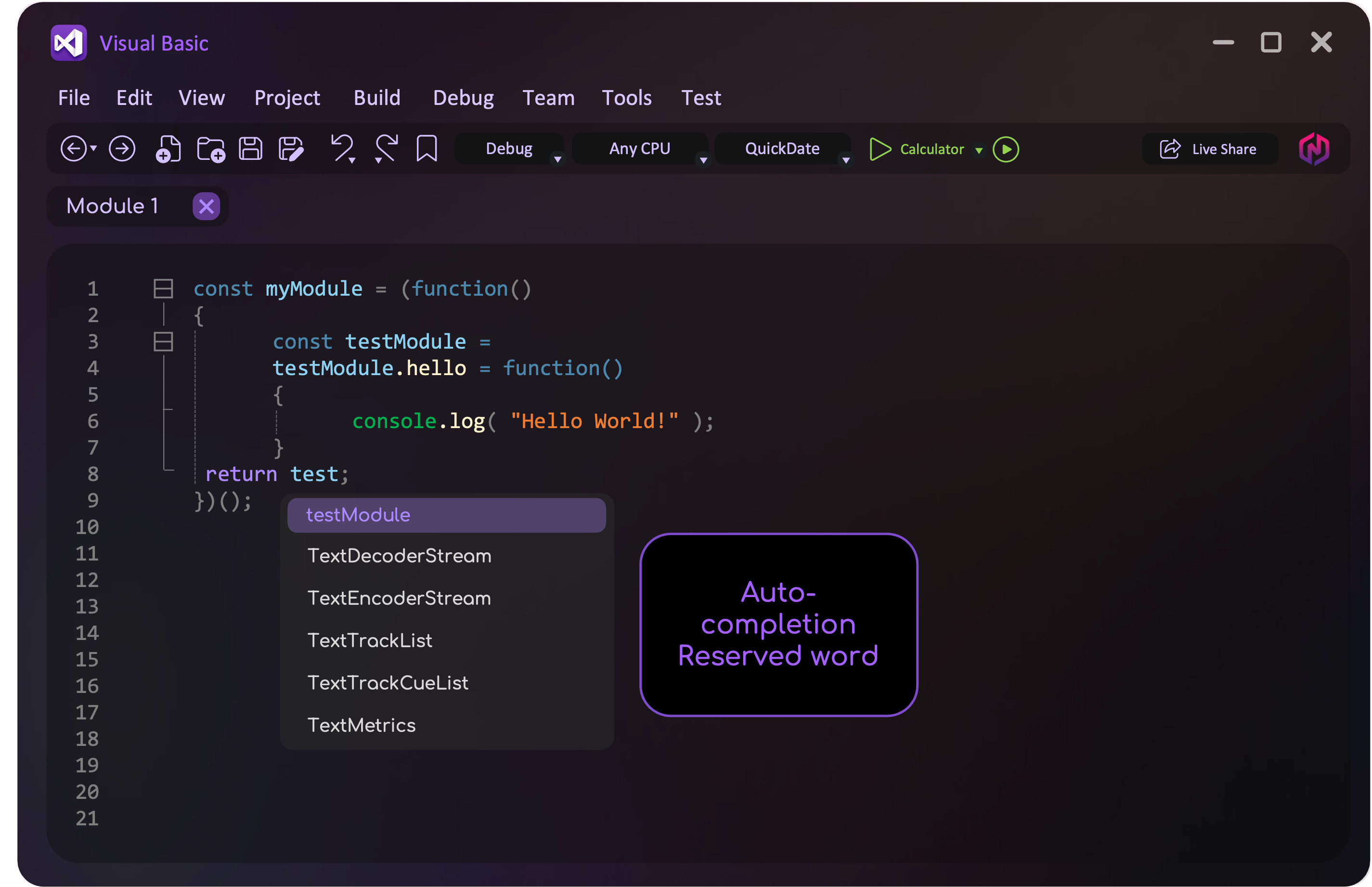
Auto-completion and Debuggers
A debugger is a tool that runs the program being developed and enables the programmer to go through the code step by step (single stepping) or pause the execution at a specific point in the source code using breakpoints. A report window then displays the values of variables and expressions evaluated at that point, helping the programmer identify logic errors and ensure the program functions as intended. On the other hand, Auto-completion can provide context-specific suggestions and autocomplete features for variable names and reserved words.
From Text Books
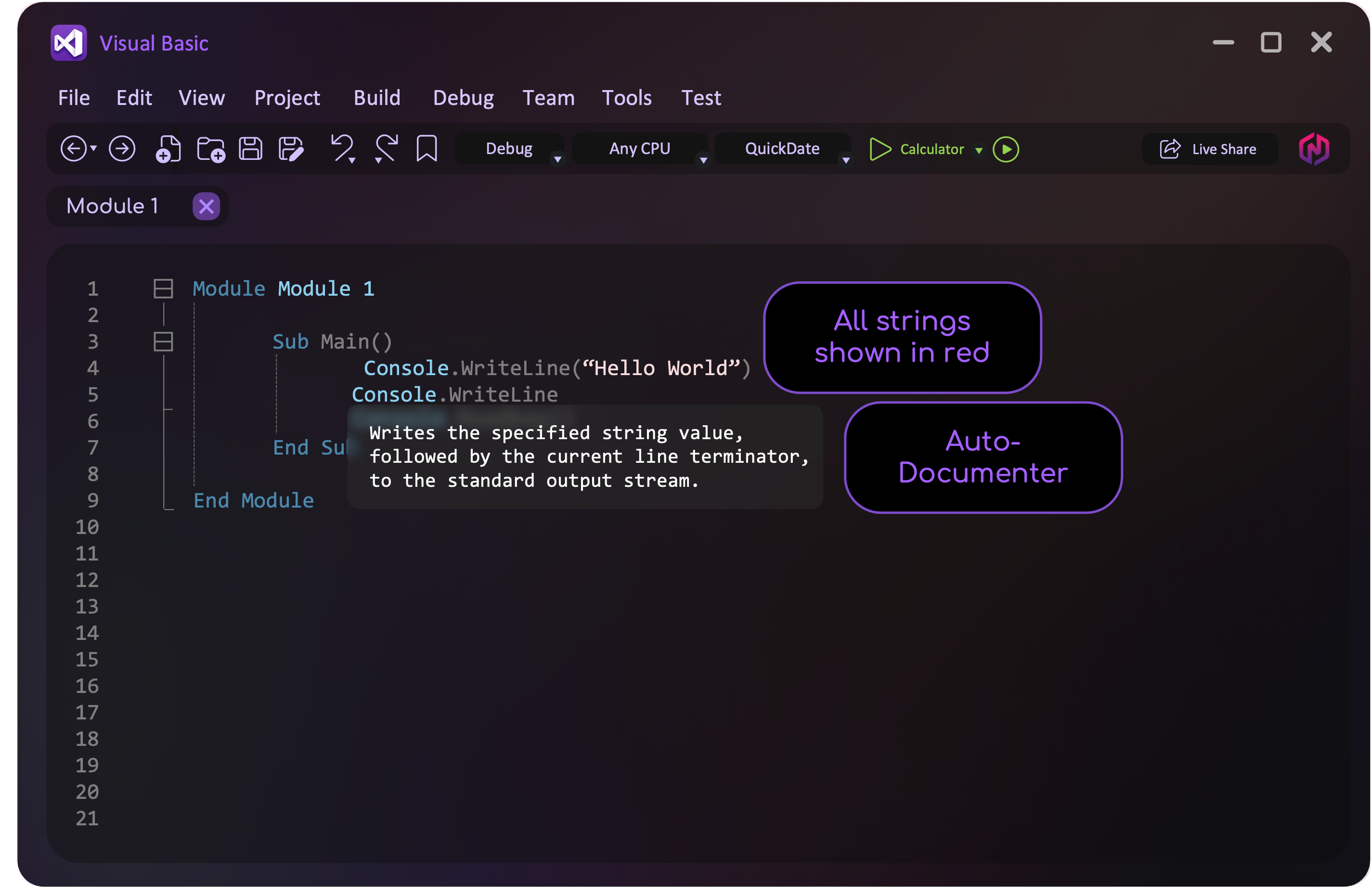
Auto-documenter and Pretty printing
IDEs may include an auto-documenter to describe the function and purpose of programming code. Additionally, many code editors use color-coding for words in the program and arrange the code in a clear and organized manner, a practice known as prettyprinting.
From Text Books
© Copyright 2024 - Made with Passion
