Methods of Data Transmission
Components of a Packet
Data sent over long distances is usually broken up into data packets. A packet consists of Header, Payload and Trailer. Each Packet has around 64KiB of data.
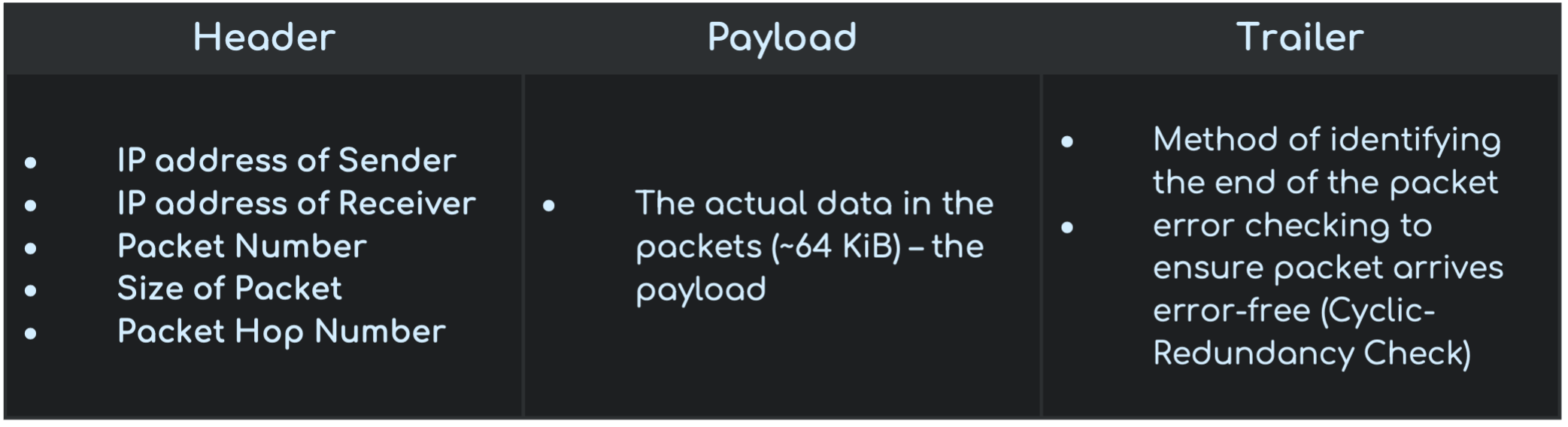
From Text Books
Cyclic-Redundancy Checks
- This involves the sending computer adding up all the 1-bits in the payload and storing this as a hex value in the trailer before it is sent.
- Once the packet arrives, the receiving computer recalculates the number of 1-bits in the payload.
- The computer then checks this value against the one sent in the trailer.
- If the two values match, then no transmission errors have occurred; otherwise, the packet needs to be re-sent.
From Text Books
Packet Switching
Data is broken/split/divided into packets (P1). Each packet takes a different route (P2). A router controls the route/path a packet takes (P3). The Router selects the shortest/fastest available route/path (P4). The Packets may arrive out of order (P5). Once the last packet has arrived, packets are reordered (P6). If a packet is missing/corrupted, it is requested again (P7).
From Text Books
Advantages and Disadvantages of Packet Switching
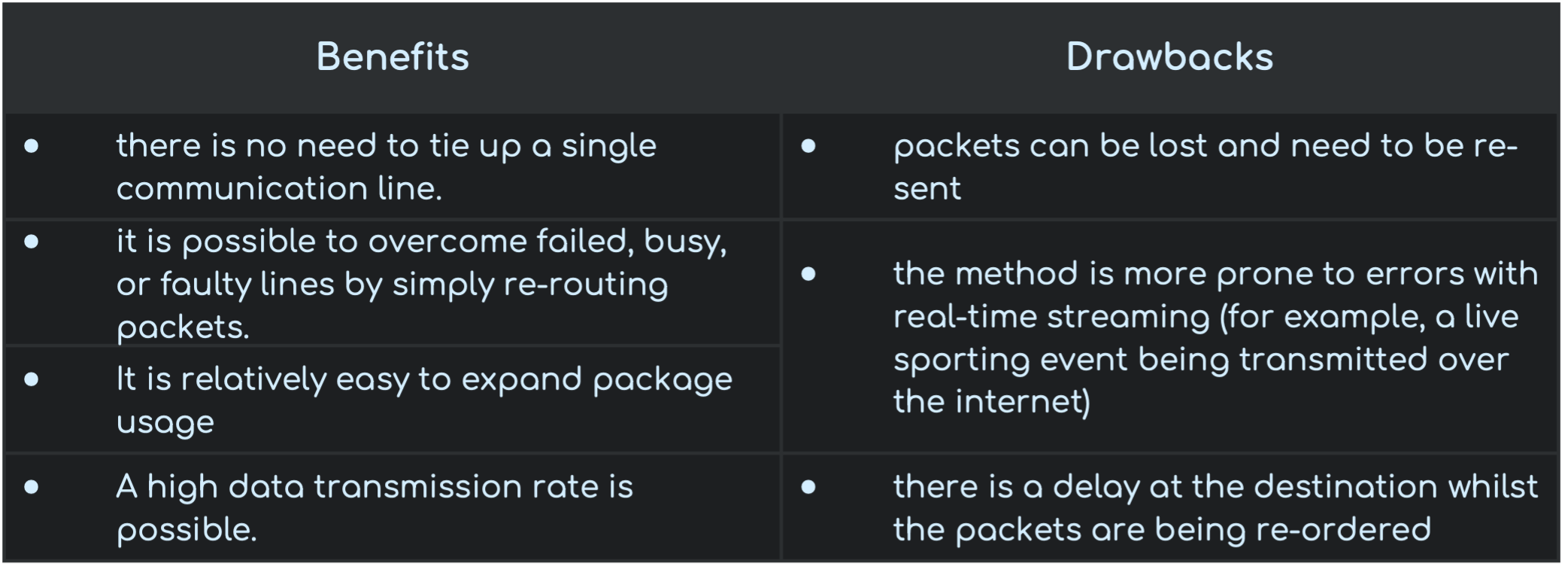
From Text Books
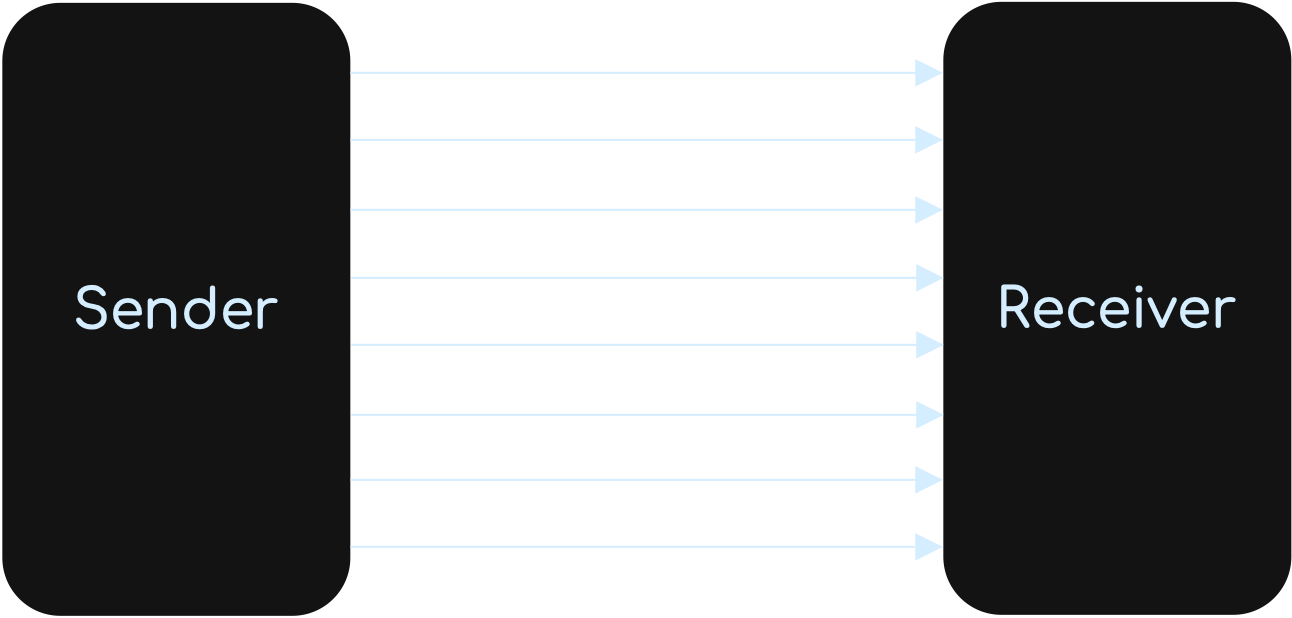
Data Transfer
Simplex Data Transfer occurs when data can be sent in one direction only (from ‘A’ to ‘B’ only or ‘B’ to ‘A’ only). An example of this would be sending data from a computer to a printer.
Half-duplex Data Transfer occurs when data is sent in both directions but not at the same time (data can be sent from ‘A’ to ‘B’ and from ‘B’ to ‘A’, but the data can’t be transferred at the same time). An example of this would be a walkie-talkie, where a message can be sent in one direction only at a time; but messages can be both received and sent.
Full-duplex Data Transfer occurs when data can be sent in both directions at the same time (data can be sent from ‘A’ to ‘B’ and from ‘B’ to ‘A’ along the same transmission line simultaneously). An example of this would be a broadband internet connection.
From Text Books
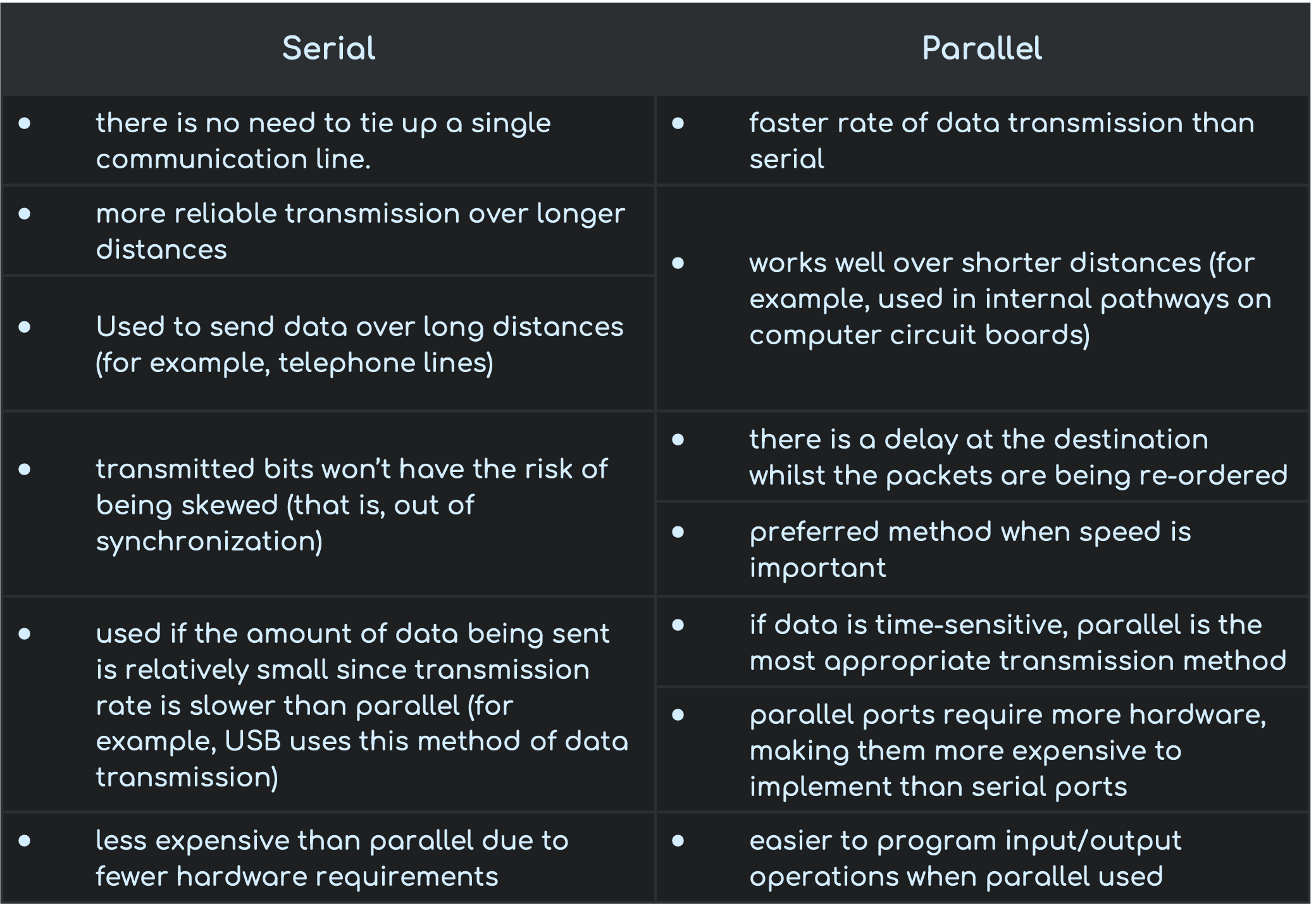
Serial and parallel Data Transfer
Serial data transmission occurs when data is sent one bit at a time over a single wire/channel. bits are sent one after the other as a single stream.

Parallel data transmission occurs when several bits of data (usually one byte) are sent down several channels/wires all at the same time. each channel/wire transmits one bit.
From Text Books
Comparison Between Serial and Parallel
From Text Books
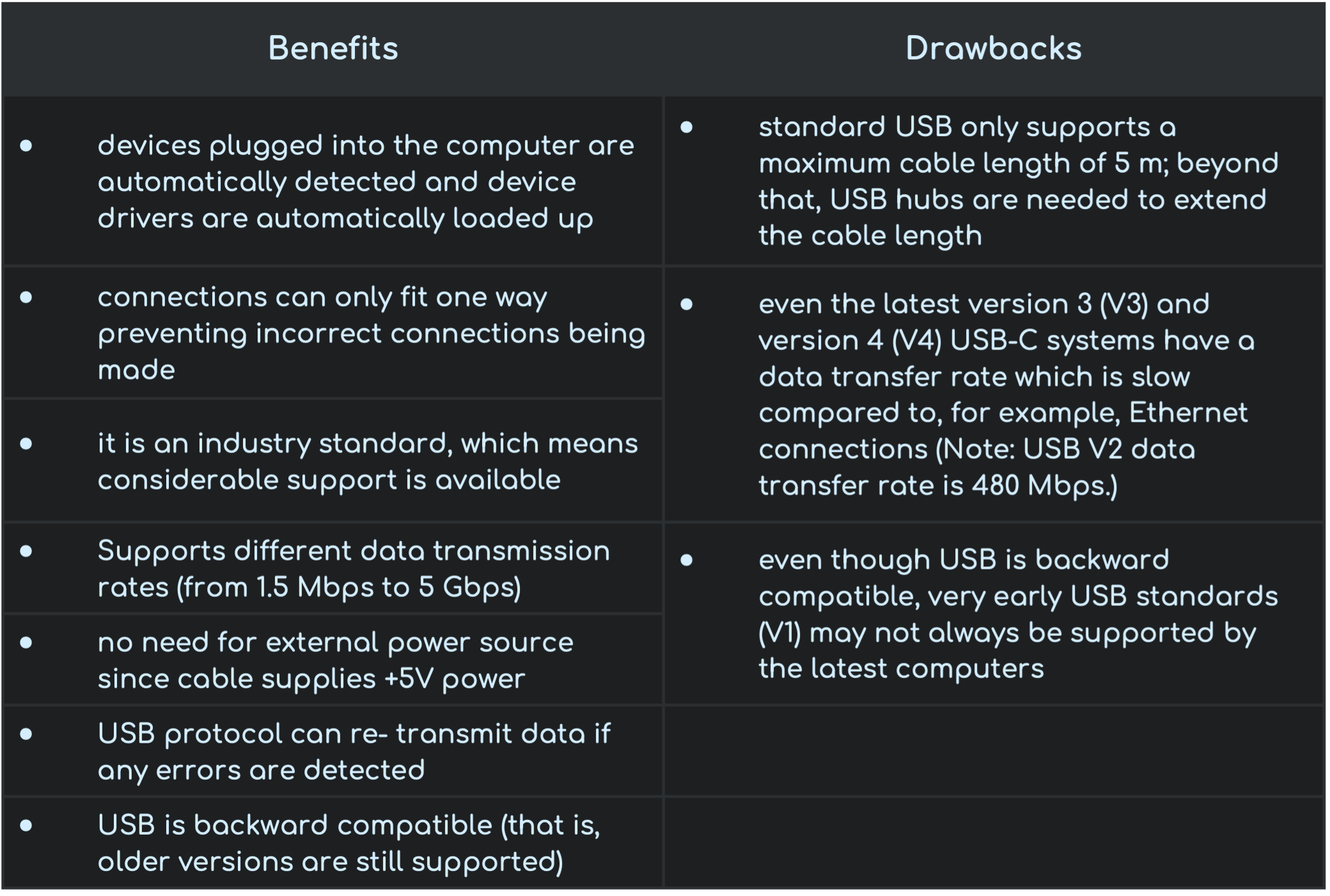
Advantages and Disadvantages of USB
From Text Books
Methods of Error
Detection
Parity Check
Checks a byte of data (P1). The check is performed when data is received (P2). First, A parity bit is added (to the parity byte) (P3). Counts/checks number of 1’s (counts/checks to see if 1’s are even OR counts/checks to see if 1’s are odd) (P4). A Parity byte can be even or odd (P5). If parity is incorrect, error is detected (P6).
From Text Books
Check Digit
A digit that is calculated from the data / uses modulo to calculate digit (P1). It is appended / added to the data (P2). Digit is recalculated when data is entered (P3). Digits are compared to check for error (P4).
From Text Books
Check Sum
A value is calculated from the data (P1). The value is then transmitted with the data (P2). The value is recalculated after transmission (P3). Values are compared after transmission to check for error (P4).
From Text Books
Automatic Repeat reQuest (ARQ)
Uses acknowledgement / request and time-out (P1). Check performed on receiving data // error is detected by e.g. parity check, check sum (P2). If error detected, request is sent to resend data // negative acknowledgement is used (P3).Resend request is repeated till data is sent correctly / requests time out / limit is reached (P4). Send acknowledgement that data is received // positive acknowledgement is used (P5). If acknowledgement not received in set time data is resent (P6).
From Text Books
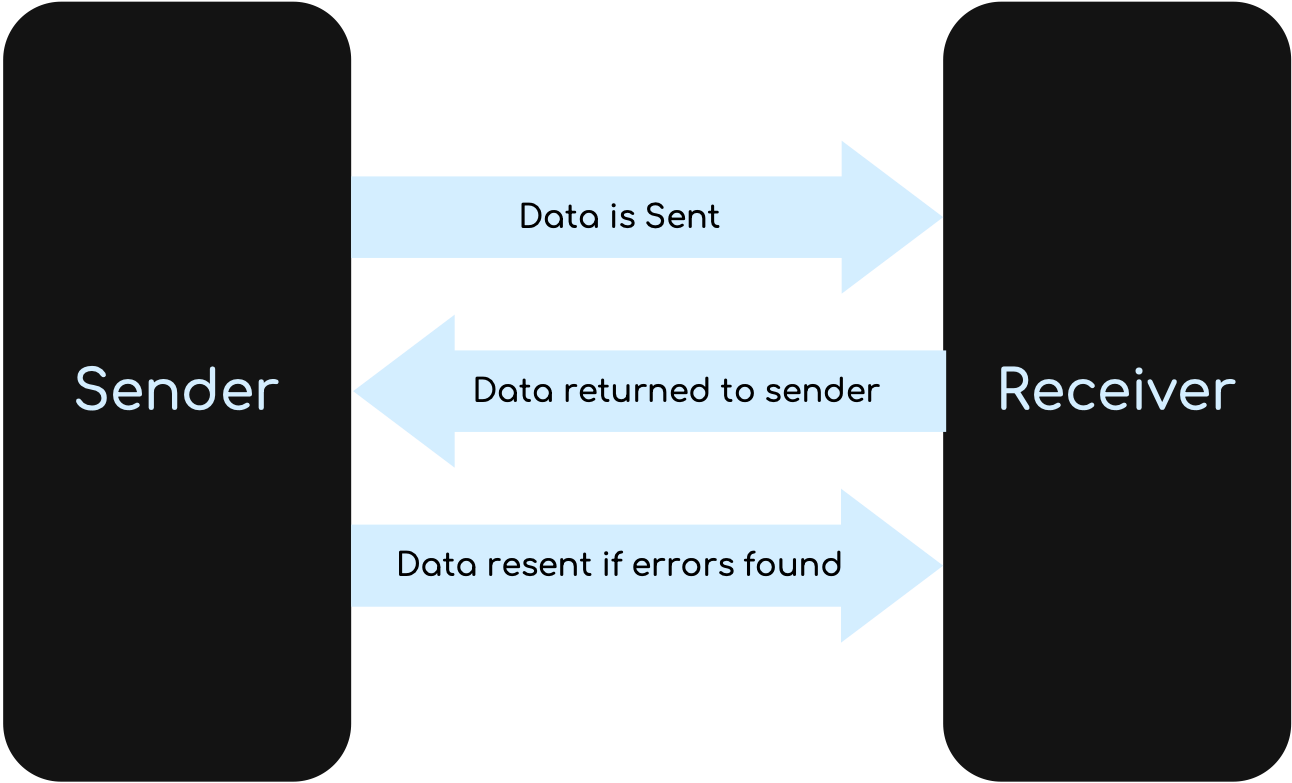
Echo Check
Data is sent to the receiver and then a copy of the data is sent back to the sender (P1). The returned data is compared with the original data by the sender’s computer (P2). If there are no differences, then the data was sent without error (P3). If the two sets of data are different, then an error occurred at some stage during the data transmission (P4).
From Text Books
Encryption
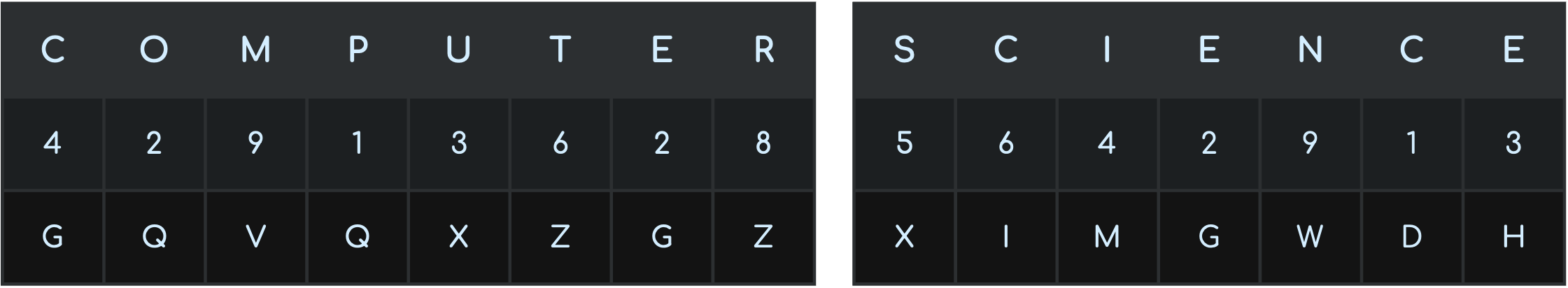
Symmetric Encryption
Symmetric encryption uses an encryption key; the same key is used to encrypt and decrypt the encoded message. An Example: In this example, the encryption key used is:
4 2 9 1 3 6 2 8 5 6
From Text Books
Asymmetric Encryption
From Text Books
- The receiver uses an algorithm to generate a matching pair of keys (private and public) that they must keep stored on their computers; the matching pairs of keys are mathematically linked but can’t be derived from each other.
- The receiver now sends the public key to the sender.

- The sender now uses the receiver’s public key to encrypt the document. The sender sends his encrypted document (ciphertext) back to the receiver.
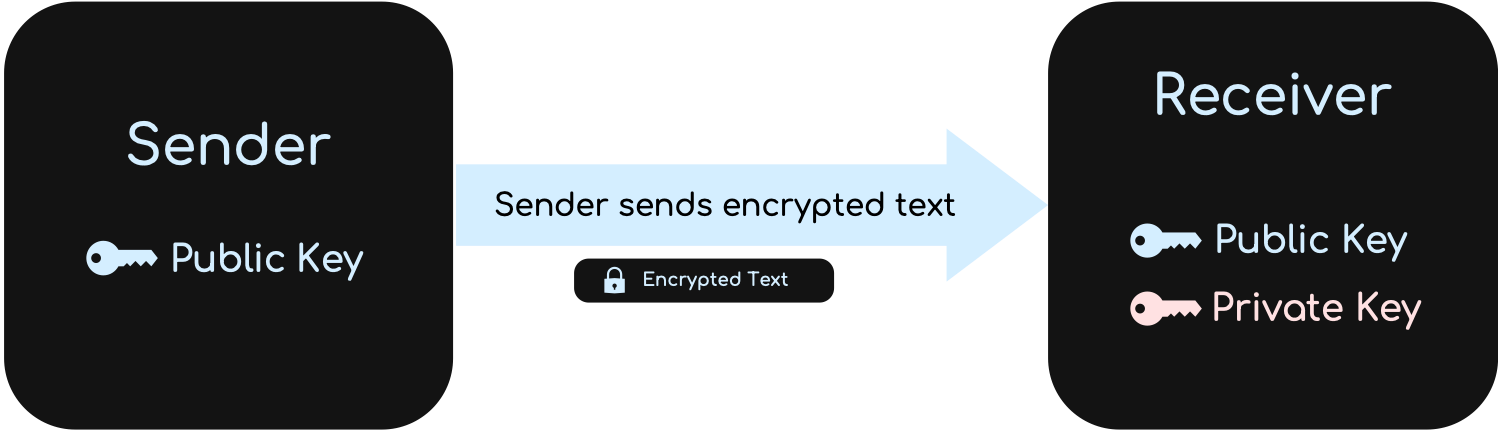
- The receiver uses their matching private key to unlock the sender’s document and decrypt it; this works because the public key used to encrypt the document and the private key used to decrypt are a matching pair generated on the receiver’s computer.
© Copyright 2024 - Made with Passion
